Vulnerability & Penetration Testing Services
Full Width Page
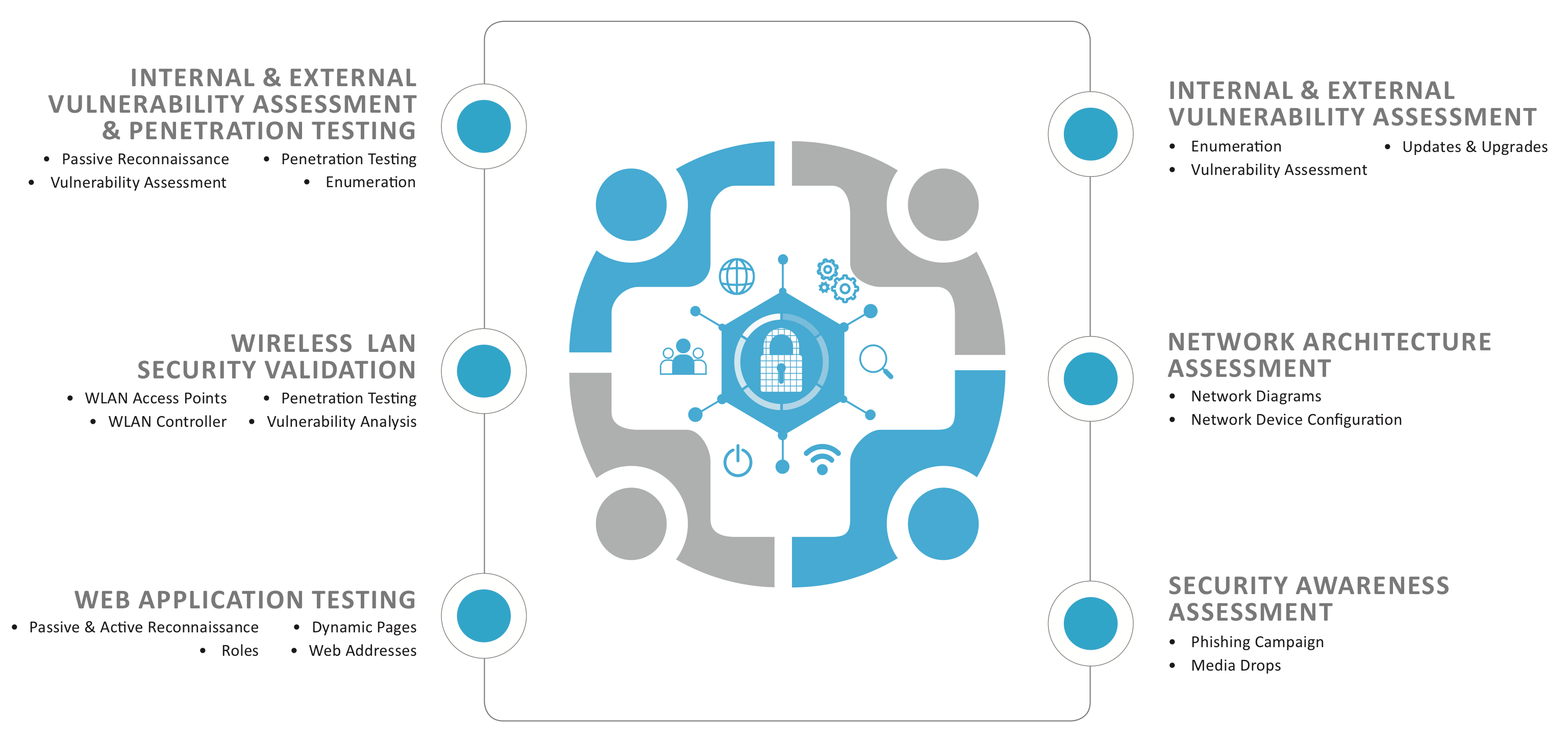
Our penetration testing services team will simulate a real-world attack on your networks, applications, devices, and/or people to demonstrate the security level of your key systems and infrastructure and show you what it will take to strengthen it.
Our Approach
Typically, penetration tests result is a long list of problems with little context on how to fix them or where to start. The Trustsec team employs the DREAD methodology (Damage, Reproducibility, Exploitability, Affected Users, & Discoverability) to provide a prioritized list of issues, based on the damage potential and threat severity.
What we provide
A detailed description and proof of concept for each finding, as well as an actionable remediation plan. And because we understand that risk severity is only one factor in prioritizing remediation efforts, we'll also provide insight into the level of effort needed to remediate the findings.
We're able to simulate real-world attacks in order to provide a snapshot-in-time assessment of vulnerabilities and threats to your network infrastructure.
Web application Penetration testing Services
Our team leverages several frameworks in order to provide an accurate and timely assessment of web-based application security. We support the Open Source Security Testing Methodology Manual (OSSTMM) and the Penetration Testing Execution Standard (PTES). We also leverage OWASP (Open Web Application Security Project) as a baseline to validate test results against.
